Figure 5-1. Netmask example showing addresses and masks in decimal, hexadecimal, and binary
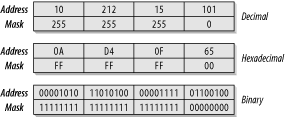
IP network addresses consist of 4 octets (8-bit bytes). The standard notation for this address is to express each octet as a decimal number from 0 to 255, separated by dots (dotted-decimal notation), for example, 10.212.15.101. Because groups of these IP addresses identify network segments, it must be possible to express ranges of addresses in a simple summary notation. Using a netmask expresses these ranges. The netmask is another 4-octet number that is also often expressed as decimal numbers separated by dots. However, it is actually easiest to understand the meaning of the netmask in its binary representation.
Each 1 bit in the netmask indicates that the corresponding bit in the IP address is part of the network address. Each 0 bit in the netmask similarly identifies a host part of the address. As shown in Figure 5-1, if the address 10.212.15.101 has a mask of 255.255.255.0, then the network portion of the address is 10.212.15.0 and the host portion is just the last 101.

The netmask can also create larger or smaller networks. If the mask is 255.0.0.0, then you can put a large number of hosts on a small number of networks. Similarly, a mask of 255.255.255.252 allows a very small number of hosts and potentially more networks. The smaller networks that can be created this way are called subnets. Depending on the mask, though, not all IP addresses are usable.
Consider the common example where the netmask is 255.255.255.0, and assume that the network address is 10.212.15.0. As a result, the first usable host address in this range is 10.212.15.1 and the last one is 10.212.15.254.
The general rule is that you cannot use addresses that have either all ones or all zeros in the binary expression of the host parts of their addresses because these addresses are reserved for local broadcast purposes. Consider a subnet with a mask of 255.255.255.252 whose address is 10.212.15.100. The first available address to use on this subnet is 10.212.15.101. The last one is 10.212.15.102. Thus, this network segment can only have two devices on it.
Table 5-1 shows the number of host addresses available for several commonly used netmask options.
|
Netmask |
Host bits available |
Number of hosts |
Applications |
|---|---|---|---|
|
255.255.255.255 |
0 |
1 |
Host mask |
|
255.255.255.252 |
2 |
2 |
Point-to-point links |
|
255.255.255.248 |
3 |
6 |
Small special-purpose segments |
|
255.255.255.240 |
4 |
14 |
Small special-purpose segments |
|
255.255.255.224 |
5 |
30 |
Medium-sized segments |
|
255.255.255.192 |
6 |
62 |
Rarely used |
|
255.255.255.128 |
7 |
126 |
Rarely used |
|
255.255.255.0 |
8 |
254 |
General-purpose segments |
Notice that the first entry in this table, the one with netmask 255.255.255.255, has a binary representation that is all ones. In effect, the entire address is a network address. Clearly, this leaves no room for host addresses, but that doesn't mean that you can't configure a host on this network; you just can't differentiate between the hosts that are within a particular network using this address. As long as only one host is in the network, there is no conflict.
How can there be a network with only one host? What will that host send its packets to in order to get to other networks? Paradoxically, this netmask can be quite useful; it is typically used as a loopback address, for example. This is a purely internal address within a host that can be used for special purposes such as management. It is also common to use a loopback address for tunnel terminations, since this loopback interface is always guaranteed to be active, even if the device itself is on a backup circuit. Loopback addresses are also often used in conjunction with dial backup applications.
The 192 and 128 masks are rarely used for subtle compatibility reasons. This has to do with the closely related concepts of multiple subnet broadcasting and address classes. These concepts are now considered optional parts of the IP Core standard. I discuss these issues later in this chapter.
At one time it was fashionable to use more complicated subnet masks. Instead of just using masks that had all ones up to a certain bit, usually in the last octet, some large networks used masks such as 255.255.255.56, for which the bit pattern in the last octet is 00111000. The idea of these masks was to provide a way to open up a smaller address range. For example, the engineer could start with a mask of 255.255.255.248 (11111000). She might initially assign a particular Ethernet segment the subnet 192.168.1.16. Then, as that segment grows beyond the 6 available addresses, she could give it an additional block by just changing the subnet mask to 255.255.255.120 (01111000). The available range of addresses now includes 192.168.1.17-23 and 192.168.1.144-150. The range from 17 to 23 is the addresses that have the 0 bit in the first position. The address 144-150 has a 1 in this bit position. Table 5-2 shows why this works.
|
First three octets |
Last octet |
Binary last octet |
Comment |
|---|---|---|---|
|
255.255.255. |
120 |
0-1111-000 |
Mask |
|
192.168.1. |
16 |
0-0010-000 |
All zeros |
|
192.168.1. |
17 |
0-0010-001 |
First address available |
|
192.168.1. |
23 |
0-0010-111 |
Last address, first half |
|
192.168.1. |
144 |
1-0010-000 |
First address, last half |
|
192.168.1. |
150 |
1-0010-110 |
Last address available |
|
192.168.1. |
151 |
1-0010-111 |
All ones |
This procedure of subnetting is called "counting from the left." While it is effective, it is not commonly used anymore for several reasons. First, how the range from 17-23 is connected to the range from 144-150 confuses most casual observers. This confusion will invariably make troubleshooting much more difficult than it needs to be. Second, if you really want to use this scheme, then you have to set the second range aside just in case you need it later. If you think you might need more addresses, though, why not just assign larger subnets in the first place? The third reason to avoid using this sort of scheme is that specifying a subnet mask by just counting the one-bits has become commonplace. So the mask 255.255.255.240 would be the 28-bit mask. It is common to specify the subnet 192.168.1.16 with this mask as 192.168.1.16/28. But 255.255.255.120 also has 28 bits of ones, so there is a risk of confusing these two networks.
Finally, this type of subnetting scheme clearly breaks one of network design's Core principles. It is inherently complicated and difficult to understand. Simplicity is always the best policy in network design.
Some networks may still use a counting-from-the-left subnetting scheme. This scheme is used because, once started, it would be difficult to get away from it without readdressing large numbers of end devices. However, I believe that this technique is not good, and I recommend migrating away from it if possible.