| [ Team LiB ] |
|
1.2 Windows NT Versus Active DirectoryAs we mentioned earlier, Windows NT and Active Directory both provide directory services to clients (Windows NT in a more generic sense). And while both share some common concepts, such as Security Identifiers (SIDs) to identify security principals, they are very different from a feature, scalability, and functionality point of view. Table 1-1 contains a comparison of features between Windows NT and Active Directory.
First, Windows NT Primary Domain Controllers and Backup Domain Controllers have been replaced by Active Directory Domain Controllers. It is possible under Active Directory to promote member servers to Domain Controllers (DCs) and demote DCs to ordinary member servers, all without needing a reinstallation of the operating system; this is not the case under Windows NT. If you want to make a member server a DC, you can promote it using the dcpromo.exe wizard. dcpromo asks you a number of questions, such as whether you are creating the first domain in a domain tree or joining an existing tree, whether this new tree is part of an existing forest or a new forest to be created, and so on. Organizational Units are an important change with Active Directory. Under Windows NT, administration was delegated on a per-domain basis, while under Active Directory, both Organizational Units and domains can be used as administration boundaries. This can significantly reduce the number of domains you require. Windows NT used NetBIOS as its primary network communication mechanism, whereas Active Directory is tightly integrated with DNS and uses TCP/IP. Under previous versions, administrators ended up maintaining two computer lookup databasesóDNS for name resolution and WINS for NetBIOS name resolutionóbut Active Directory no longer does traditional NetBIOS name resolution. Instead, it relies on DNS. You can still install and run a WINS server, but this would be only for backward compatibility until all your machines and applications are upgraded. The significant difference in replication is that Active Directory will replicate at the attribute rather than object level. With Windows NT, if you changed the full name of a user object, the whole object had to be replicated out. In the same scenario with Active Directory, only the modified attribute will be replicated. Coupled with some very clever changes to the way replication works, this means that you replicate less data for shorter periods, thereby reducing the two most important factors in replication. See Chapter 5 and Chapter 9 for more on replication. The suggested maximum Windows NT SAM was 40 MB, which was roughly equivalent to about 40,000 objects, depending on what proportion of computer, user, and group accounts you had in your domain. Many companies have gone above 75 MB for the SAM for one domain due to the huge number of groups that they were using, so this rule was never hard and fast as long as you understood the problems you were likely to experience if you went past the limit. However, Active Directory is based on the Extensible Storage Engine (ESE) database used by Exchange and developed to hold millions of objects with a maximum database size of 70 TB. This should be enough for most people's needs and is also only a recommended maximum limit. Remember, however, that this new database holds all classes of objects, not just the users, groups, and computers of the previous version's SAM. As more and more Active Directory-enabled applications are developed, more classes of objects will be added to the schema, and more objects will be added to the directory. To bring this into perspective, imagine that one of the world's largest aerospace companies has around half a million computers. Assuming an equivalent number of staff, this still uses only 10% of the maximum database capacity. However, when you begin to consider all the other objects that will be in Active Directory, including file shares, printers, groups, organizational units, domains, contacts, and so on, you can see how that percentage will increase. For administrators of Windows NT, the significant increase in scalability may be the most important change of all. It was extremely easy to hit the 40 MB SAM limit within an NT domain, forcing you to split the domain. You ended up managing multiple domains when you really didn't want to. It was frustrating. None of the domains were organized into a domain tree or anything of the sort, so they had no automatic trusts between them. This meant that NT administrators had to set up manual trusts between domains, and these had to be initiated at both domains to set up a single one-way trust. As you added more domains, you ended up managing even greater numbers of trusts. To counter this problem, Microsoft introduced four domain models that you could use as templates for your Windows NT design: the single-domain model, the single-master domain model, the multimaster domain model, and the complete-trust domain model. All four are shown in Figure 1-1. The most common model after the single-domain model is probably the multimaster domain model. Figure 1-1. The four Windows NT domain models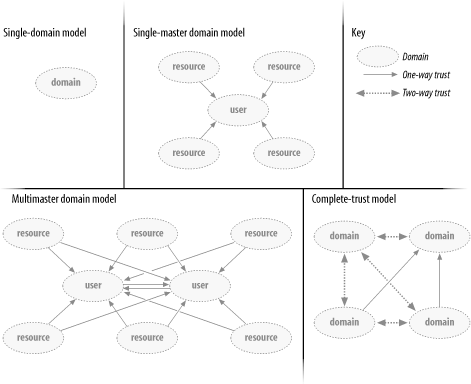 Stated very simply, the single-domain model had, as the name implied, only one domain with a SAM smaller than 40 MB and no trusts. Where multiple domains were needed for resource access but the SAM was still less than 40 MB, the single-master domain model was used. The single-master domain model was made up of one user domain and multiple resource domains. The important point was that the resource domains had one-way trusts with the user domain that held all the accounts. Due to the one-way trusts, the administrators of the resource domains could set permissions as they wished to their own resources for any accounts in the user domain. This meant that one central set of administrators could manage the accounts, while individual departments maintained autonomy over their own resources. When the SAM was going to grow past 40 MB, a multimaster model came into play. The administrators of the user domain split the user accounts into two or more domains, giving them two-way (i.e., complete) trust between each other, and then each resource domain had to have a one-way trust with each user domain. Scaling this up, for a multimaster domain with 10 user domains and 100 resource domains, that's 90 trusts to make up the intra-user trusts and 1,000 separate resource-to-user trusts that must be manually set. Finally, in some cases, the complete-trust model was used where any domain could create accounts and allocate resources to any other domain. Active Directory acts like a single-master domain model in which the Organizational Units function as the resource domains. As you can see, this eliminates the need for maintaining separate Windows NT resource domains, as these can be converted to Organizational Units in what was the user domain. All Active Directory domains within a forest trust each other via transitive trusts. In Windows Server 2003 Active Directory, transitive forest trusts are also available so that the domains in two different forests can completely trust each other via a single explicit trust between the forest root domains. Finally, the Windows NT schema was not extensible. No new object types could be added to it, which was a significant limitation for most enterprises. When Microsoft products that extended Windows NTósuch as Terminal Server and File and Print for NetWareówere released, each had to store any attribute data that it wanted all together within one existing attribute. Under Active Directory, the schema is fully extensible, so any new products can extend the schema and add in objects and attributes as required.
|
| [ Team LiB ] |
|