| [ Team LiB ] |
|
13.4 FSMO RecoveryThe FSMO roles were described in Chapter 2. These roles are considered special in Active Directory because they are hosted on a single domain controller within a forest or domain. The architecture of Active Directory is highly redundant, except for FSMO roles. It is for this reason that you need to have a plan on how to handle FSMO failures. It would be a really nice feature if domain controllers could detect that they are being shut down and gracefully transfer any FSMO roles to other domain controllers. In fact, the Active Directory development team is considering this feature for the next major release of Active Directory after Windows Server 2003, but that is a ways out. Without having the graceful FSMO role transfer, you have to do manual transfers. Manually transferring a role is pretty straightforward. You bring up the appropriate Active Directory snap-in, bring up the FSMO property page, select a new role owner, and perform the transfer. Here is a list of the FSMO roles and the corresponding snap-in that can be used to transfer it to another domain controller:
Figure 13-9 shows the Active Directory Domains and Trusts screen for changing the Domain Naming FSMO. Figure 13-9. Changing the Domain Naming FSMO role owner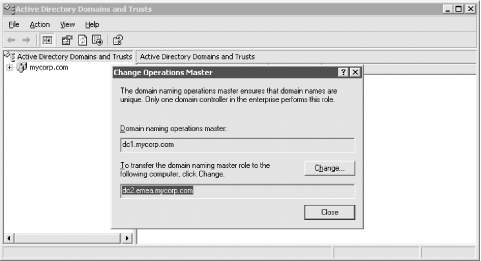 When a FSMO role owner goes down and cannot be brought back online, you no longer can transfer the role; you instead have to "seize" it. And unfortunately you cannot seize FSMO roles using the Active Directory snap-ins as you can to transfer them. To seize a FSMO role you need to use the ntdsutil utility that we used earlier to do restores. We will now walk through the ntdsutil commands that are used to seize a FSMO role. Note that due to the width of the output, some of the text wraps to the following line. We first start off by getting into the ntdsutil interactive mode and looking at the options for the roles command. C:\> ntdsutil
ntdsutil: roles
fsmo maintenance: ?
? - Show this help information
Connections - Connect to a specific domain controller
Help - Show this help information
Quit - Return to the prior menu
Seize domain naming master - Overwrite domain role on connected server
Seize infrastructure master - Overwrite infrastructure role on connected server
Seize PDC - Overwrite PDC role on connected server
Seize RID master - Overwrite RID role on connected server
Seize schema master - Overwrite schema role on connected server
Select operation target - Select sites, servers, domains, roles and
naming contexts
Transfer domain naming master - Make connected server the domain naming master
Transfer infrastructure master - Make connected server the infrastructure master
Transfer PDC - Make connected server the PDC
Transfer RID master - Make connected server the RID master
Transfer schema master - Make connected server the schema master
We must now connect to the domain controller to which we want to seize the role. In this case, we will connect to DC1. fsmo maintenance: connections server connections: connect to server dc1 Binding to dc1 ... Connected to dc1 using credentials of locally logged on user. server connections: quit At this point we can transfer and seize any available FSMO role to the DC1 domain controller. In the next example, we will attempt to seize the Schema Master. The current Schema Master is DC2. If we tried to perform a seizure and DC2 was operational, we would effectively do a graceful transfer of the role to DC1. If DC2 is not available then, a seizure will take place, as shown in the following output (note that some lines may wrap due to their length): fsmo maintenance: seize schema master Attempting safe transfer of schema FSMO before seizure. ldap_modify_sW error 0x34(52 (Unavailable). Ldap extended error message is 000020AF: SvcErr: DSID-03210300, problem 5002 (UNAVAILABLE), data 1753 Win32 error returned is 0x20af(The requested FSMO operation failed. The currentFSMO holder could not be contacted.) ) Depending on the error code this may indicate a connection, ldap, or role transfer error. Transfer of schema FSMO failed, proceeding with seizure ... Server "dc1" knows about 5 roles Schema - CN=NTDS Settings,CN=DC1,CN=Servers,CN=RTP,CN=Sites,CN=Configuration,DC=mycorp,DC=com Domain - CN=NTDS Settings,CN=DC1,CN=Servers,CN=RTP,CN=Configuration, DC=mycorp,DC=com PDC - CN=NTDS Settings,CN=DC1,CN=Servers,CN=RTP,CN=Sites,CN=Configuration, DC=mycorp,DC=com RID - CN=NTDS Settings,CN=DC1,CN=Servers,CN=RTP,CN=Sites,CN=Configuration, DC=mycorp,DC=com Infrastructure - CN=NTDS Settings,CN=DC1,CN=Servers,CN=RTP,CN=Sites,CN=Configuration, DC=mycorp,DC=com Note that a connection is first attempted to the current role owner, and if it cannot be reached, ntdsutil does the seizure. One of the nice features of the quirky ntdsutil command is that it can be run in interactive mode as we just showed, or it can be run from a single command line. To accomplish the same seizure using a single command line, the command would look as follows: C:\> ntdsutil roles conn "co to ser dc1" q "seize schema master" q q Depending on your needs, you could write a batch script pretty easily to prompt for the role you want to seize and the DC to transfer or seize the role to. This could help when it gets down to crunch time, you need to seize the role quickly, and you do not want to thumb through this book trying to find all of the commands. |
| [ Team LiB ] |
|