19.1 Objective 1: Fundamentals of
TCP/IP
The TCP/IP suite of protocols was
adopted as a military standard in 1983 and has since become
the world standard for network communications on the Internet
and on many LANs, replacing proprietary protocols in many
cases. Much has been written about TCP/IP and the history of
the Internet. This section includes only material cited by LPI
Objectives.
19.1.1 Addressing and Masks
The early specification of the Internet Protocol (IP) recognized that
it would be necessary to divide one's given allotment of IP
addresses into manageable sub-networks. Such division allows
for distributed management, added security (fewer hosts can
potentially snoop network traffic), and the use of multiple
networking technologies (Ethernet, Token Ring, ATM, etc.). IP
also enables convenient partitioning of the physical portions
of a network across physical and geographical boundaries. To
provide the capability to locally define networks, IP addresses are
considered as having two distinct parts: the part that
specifies a subnet and the one that specifies a network
interface. The boundary
between the network and host portions of an IP address is
delineated by a subnet mask,
required by the TCP/IP configuration
of any network interface. Like the IP address, the subnet mask
is simply a 32-bit number specified in four 8-bit segments
using dotted quad decimal
notation. The familiar class A, B, and C networks have
these subnet masks:
- Class A: 255.0.0.0 (binary
11111111.00000000.00000000.00000000)
-
8-bit network address and 24-bit host
address
- Class B: 255.255.0.0 (binary
11111111.11111111.00000000.00000000)
-
16-bit network address and 16-bit host
address
- Class C: 255.255.255.0
(binary 11111111.11111111.11111111.00000000)
-
24-bit network address and 8-bit host
address
When logically AND'd with an IP address, the
bits set to in the subnet mask obscure the host portion of the
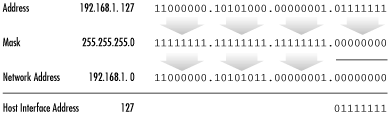
address. The remaining bits represent the network address. For example, a host on a class C
network might have an IP address of 192.168.1.127. Applying
the class C subnet mask 255.255.255.0, the network addressof
the subnet would be 192.168.1.0, and the host address would be
127, as depicted in Figure
19-1.
While it is typical to use the predefined
classes (A, B, and C), the boundary can be moved left or right
in the IP address, allowing for fewer or more subnets,
respectively. For example, if a single additional bit were
added to the class C subnet mask, its IP address would be:
- 255.255.255.128 (binary
11111111.11111111.11111111.10000000)
-
25-bit network address and 7-bit host
address
With such a subnet defined on an existing
class C network such as 192.168.1.0, the 256-bit range is
split into two subnets, each with seven host bits. The first
of the two subnets begins at 192.168.1.0 (the subnet address)
and continues through 192.168.1.127 (the subnet broadcast
address). The second subnet runs from 192.168.1.128 through
192.168.1.255. Each of the two subnets can accommodate 126
hosts. To extend this example, consider two additional bits:
- 255.255.255.192 (binary
11111111.11111111.11111111.11000000)
-
26-bit network address and 6-bit host
address
When applied to a class C network, four
subnets are created, each with six host bits. Just as before,
the first subnet begins at 192.168.1.0 but continues only
through 192.168.1.63. The next subnet runs from 192.168.1.64
through 192.168.1.127 and so on. Each of the four subnets can
accommodate 62 hosts. Table
19-1 shows more detail on class C subnets, considering
only the host portion of the address.
Table 19-1. Class C IP Subnet Detail
|
128 |
2 |
0 |
127 |
1 |
126 |
126 |
|
| |
|
128 |
255 |
129 |
254 |
126 |
252 |
|
192 |
4 |
0 |
63 |
1 |
62 |
62 |
|
| |
|
64 |
127 |
65 |
126 |
62 |
|
| |
|
128 |
191 |
129 |
190 |
62 |
|
| |
|
192 |
255 |
193 |
254 |
62 |
248 |
|
224 |
8 |
0 |
31 |
1 |
30 |
30 |
|
| |
|
32 |
63 |
33 |
62 |
30 |
|
| |
|
64 |
95 |
65 |
94 |
30 |
|
| |
|
96 |
127 |
97 |
126 |
30 |
|
| |
|
128 |
159 |
129 |
158 |
30 |
|
| |
|
160 |
191 |
161 |
190 |
30 |
|
| |
|
192 |
223 |
193 |
222 |
30 |
|
| |
|
224 |
255 |
225 |
254 |
30 |
240 |
|
Be prepared to define network and host
addresses when provided an IP address and a subnet mask.
Practice with a few subnet sizes within at least one
classification (A, B, or C). Also, because the use of
decimal notation can cloud human interpretation of IP
addresses and masks, be ready to do binary-to-decimal
conversion on address numbers. |
As you can see, as the number of subnets
increases, the total number of hosts that can be deployed
within the original class C address range reduces. This is due
to the loss of both broadcast addresses and network addresses
to the additional subnets.
19.1.2 Protocols
TCP/IP is a suite of
protocols, including the Transmission Control Protocol (TCP),
Internet Protocol (IP), User Datagram Protocol (UDP), and
Internet Control Message Protocol (ICMP), among others. Some
protocols use handshaking (the exchange of control information
among communicating systems) to establish and maintain a
connection. Such a protocol is said to be connection-oriented and reliable, because the protocol itself
is responsible for handling transmission errors, lost packets,
and packet arrival order. A protocol that does not exchange
control information is said to be connectionless and unreliable. In this context,
"unreliable" simply means that the protocol doesn't handle
transmission problems itself; they must be corrected in the
application or system libraries. Connectionless protocols are
simpler and have less overhead than connection-oriented
protocols. TCP/IP is often said to be a stack of protocols, because protocols are
built in a hierarchy of layers.
Low-level protocols are used by higher-level protocols on
adjacent layers of the protocol stack:
- TCP
-
TCP is a
connection-oriented transport agent used by applications to
establish a network connection. TCP transports information
across networks by handshaking and retransmitting
information as needed in response to errors on the network.
TCP guarantees packet arrival and provides for the correct
ordering of received packets. TCP is used by many network
services, including FTP, Telnet, and SMTP. By using TCP,
these applications don't need to establish their own
error-checking mechanisms, thus making their design simpler
and easier to manage.
- IP
-
IP can be
thought of as the fundamental building block of the
Internet. IP, which is connectionless, defines datagrams
(the basic unit of transmission), establishes the addressing
scheme (the IP address), and provides for the routing of
datagrams between networks. IP is said
to provide a datagram delivery
service. Other higher-level protocols use IP as an
underlying carrier.
- UDP
-
UDP is a
connectionless transport agent. It provides application
programs direct access to IP, allowing them to exchange
information with a minimum of protocol overhead. On the
other hand, because UDP offers no assurance that packets
arrive at destinations as intended, software must manage
transmission errors and other problems such as missing and
incorrectly ordered packets. UDP is used by applications
such as DNS and NFS.
- ICMP
-
ICMP is a
connectionless transport agent that is used to exchange
control information among networked systems. It uses IP
datagrams for the following control, error-reporting, and
informational functions:
- Flow control
-
Sometimes
inbound traffic becomes too heavy for a receiving system
to process. In such cases, the receiving system can send a
message via ICMP to the source instructing it to
temporarily stop sending datagrams.
- Detecting unreachable
destinations
-
Various parts of network infrastructure
are capable of detecting that a network destination is
unreachable. In this case, ICMP messages are sent to the
requesting system.
- Redirecting
routes
-
ICMP is used among network components to
instruct a sender to use a different gateway.
- Checking remote
hosts
-
Hosts can transmit echo messages via ICMP
to verify that a remote system's Internet Protocol is
functioning. If so, the original message is returned. This
is implemented in the ping
command.
- PPP
-
PPP is used for
TCP/IP dialup network access via modem. The configuration
and use of PPP is described later in Objective 4.
|
You will need a general understanding
of the control messages sent via ICMP. In particular,
note that ICMP does not transmit data and that it is
used by ping.
|
19.1.3 TCP/IP Services
When an inbound
network request is made, such as that from a web browser or
FTP client, it is sent to the IP address of the server.
In addition, the request carries inside it a port number
(or just port), which is a
16-bit value placed near the beginning of a network packet.
The port number defines the type of server software that
should respond to the request. For example, by default, web
browsers send requests encoded for port 80. Web servers
"listen" to port 80 and respond to incoming requests. The
encoded port can be considered part of the address of a
request. While the IP address specifies a particular host, the port
specifies a specific service available on that host. Many port
numbers are predefined, and the list is expanded as needed to
accommodate new technologies. The official list of port number
assignments is managed by the Internet Assigned Numbers Authority
(IANA). The ports known by your system are listed in
/etc/services.
Port numbers 1
through 1023 are often referred to as privileged ports because the
services that use them often run with superuser authority.
Many of these, such as ports used for FTP (21), Telnet (23),
and HTTP (80), are often referred to as well-known ports because they
are standards. Port numbers from 1024 through 65535 (the
maximum) are unprivileged
ports and can be used by
applications run by ordinary system users.
During the initial contact, the client
includes a local, randomly selected, unprivileged port on the
client machine for the server to use when responding to the
request. Client-to-server
communications use the well-known port and the
server-to-client communications use the randomly selected
port. This Objective requires you to be familiar with the
privileged port numbers detailed in Table
19-2.
Table 19-2. Common Privileged Port
Numbers
|
20 |
FTP data |
When an FTP session is opened, the
binary or ASCII data flows to the server using port 20,
while control
information flows on port 21. During
use, both ports are managed by an ftp daemon, such as wu-ftpd or PROftpd. |
|
21 |
FTP control |
|
23 |
Telnet server |
Inbound Telnet requests are sent to
server port 23 and processed by telnetd. |
|
25 |
SMTP server |
This port is used by mail transfer
agents (MTAs) such as sendmail. |
|
53 |
DNS server |
Used by the Domain Name System server,
named. |
|
67 |
BOOTP/DHCP server |
A BOOTP, or the more commonly used,
DHCP server. |
|
68 |
BOOTP/DHCP client |
The client side for
BOOTP/DHCP. |
|
80 |
HTTP server |
Web servers, such as Apache (httpd), usually listen in on
this port. |
|
110 |
POP3 |
The Post Office Protocol (POP) is used
by mail client programs to transfer mail from a server.
|
|
119 |
NNTP Server |
This port is used by news servers for
Usenet news. |
|
139 |
NetBIOS |
Reserved for Microsoft's LAN network
manager. |
|
143 |
IMAP |
An alternate to POP3, IMAP is another
type of mail server. |
|
161 |
SNMP |
Agents running on monitored systems use
this port for access to the Simple Network Management
Protocol. |
This list is a tiny fraction of the many
well-known ports, but it may be necessary for you to know them
both by name and by number.
|
You should commit the list of ports in Table
19-2 to memory so you can recognize a type of
network connection solely by its port number. Your exam
is likely to have at least one question on how a
specific port is used. |
19.1.4 TCP/IP Utilities
The following popular applications, while not
strictly a part of TCP/IP, are usually provided along with a
TCP/IP implementation.
Syntaxdig hostname
Description
dig obtains
information from DNS servers. Note that additional
command-line arguments and options are available for dig but are beyond the scope of Exam
102.
Example$ dig redhat.com
; <<>> DiG 8.2 <<>> redhat.com any
;; res options: init recurs defnam dnsrch
;; got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6
;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 4,
;; ADDITIONAL: 5 QUERY SECTION:
;; redhat.com, type = ANY, class = IN
;; ANSWER SECTION:
redhat.com. 22h36m45s IN NS ns.redhat.com.
redhat.com. 22h36m45s IN NS ns2.redhat.com.
redhat.com. 22h36m45s IN NS ns3.redhat.com.
redhat.com. 22h36m45s IN NS speedy.redhat.com.
redhat.com. 23h48m10s IN MX 10 mail.redhat.com.
redhat.com. 23h48m10s IN A 207.175.42.154
;; AUTHORITY SECTION:
redhat.com. 22h36m45s IN NS ns.redhat.com.
redhat.com. 22h36m45s IN NS ns2.redhat.com.
redhat.com. 22h36m45s IN NS ns3.redhat.com.
redhat.com. 22h36m45s IN NS speedy.redhat.com.
;; ADDITIONAL SECTION:
ns.redhat.com. 1d23h48m10s IN A 207.175.42.153
ns2.redhat.com. 1d23h48m10s IN A 208.178.165.229
ns3.redhat.com. 1d23h48m10s IN A 206.132.41.213
speedy.redhat.com. 23h48m10s IN A 199.183.24.251
mail.redhat.com. 23h48m10s IN A 199.183.24.239
;; Total query time: 81 msec
;; FROM: smp to SERVER: default -- 209.195.201.3
;; WHEN: Wed Apr 5 03:15:03 2000
;; MSG SIZE sent: 28 rcvd: 275
Syntaxftp [options] host
...interactive commands...
Description
Establish
an interactive File Transfer Protocol (FTP) connection with
host in order to transfer binary or text files. FTP
creates an interactive dialog and allows for two-way file
transfer. The dialog includes username/password
authentication, user commands, and server responses.
Frequently used options
- -i
-
Turns off interactive prompting during
multiple file transfers (also see the prompt command).
- -v
-
Sets verbose mode, displays server
responses and transfer statistics.
Frequently used commands
- ascii, binary
-
Establish the transfer mode for files.
ASCII mode is provided to correctly transfer text among
computer architectures where character encoding differs.
- get file
-
Receive a single file from the
server.
- mget files
-
Receive multiple files from the
server.
- ls [files]
-
Obtain a directory listing from the server,
optionally listing files.
- put file
-
Send a single file to the
server
- mput files
-
Send multiple files to the
server.
- prompt
-
Toggle on and off interactive prompting
during mget and mput (also see the -i option).
- pwd
-
Print the working remote
directory.
- quit, exit
-
Cleanly terminate the FTP
session.
Example 1
Get a file from machine smp: $ ftp -v smp
Connected to smp.
220 smp FTP server (Version wu-2.4.2-VR17(1)
Mon Apr 19 09:21:53 EDT 1999) ready.
Name (smp:root): jdean
331 Password required for jdean.
Password:<password here>
230 User jdean logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls myfile
200 PORT command successful.
150 Opening ASCII mode data connection for /bin/ls.
-rw-r--r-- 1 jdean jdean 29 Jan 24 01:28 myfile
226 Transfer complete.
ftp> binary
200 Type set to I.
ftp> get myfile
local: myfile remote: myfile
200 PORT command successful.
150 Opening BINARY mode data connection for myfile
(29 bytes).
226 Transfer complete.
29 bytes received in 0.000176 secs (1.6e+02 Kbytes/sec)
ftp> quit
221-You have transferred 29 bytes in 1 files.
221-Total traffic for this session was 773 bytes in 3 transfers.
221-Thank you for using the FTP service on smp.
221 Goodbye.
Example 2
Many FTP servers are set up to receive
requests from nonauthenticated users. Such public access is
said to be anonymous. Anonymous
FTP is established just like any FTP connection, except that
anonymous is used as the username. An email address
is commonly used as a password to let the system owner know
who is transferring files: # ftp -v smp
Connected to smp.
220 smp FTP server (Version wu-2.4.2-VR17(1)
Mon Apr 19 09:21:53 EDT 1999) ready.
Name (smp:root): anonymous
331 Guest login ok, send your complete e-mail address as password.
Password: [email protected]
230 Guest login ok, access restrictions apply.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> <commands follow...>
Syntaxping hostname
Description
The ping command is used to send an ICMP
echo request to hostname and report on how long it
takes to receive a corresponding ICMP echo reply. Much like
sonar systems send a pulse (or "ping") to a target and measure
transit time, ping sends a
network packet to test the availability of a network node.
This technique is often used as a basic debugging technique
when network problems arise.
19.1.4.1 Example
Ping a remote host and terminate using Ctrl-C after five packets are
transmitted: $ ping lpi.org
PING lpi.org (209.167.177.93) from 192.168.1.30 :
56(84) bytes of data.
64 bytes from new.lpi.org (209.167.177.93):
icmp_seq=0 ttl=240 time=51.959 msec
64 bytes from new.lpi.org (209.167.177.93):
icmp_seq=1 ttl=240 time=60.967 msec
64 bytes from new.lpi.org (209.167.177.93):
icmp_seq=2 ttl=240 time=47.173 msec
64 bytes from new.lpi.org (209.167.177.93):
icmp_seq=3 ttl=240 time=46.887 msec
64 bytes from new.lpi.org (209.167.177.93):
icmp_seq=4 ttl=240 time=46.836 msec
--- lpi.org ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max/mdev = 46.836/50.764/60.967/5.460 ms
Syntaxtelnet [host] [port]
Description
Establish a
connection to host (either a system name or IP address)
using port. If a specific port is omitted, the
default port of 23 is assumed. If host is omitted,
telnet goes into an interactive
mode similar to ftp.
Syntaxtraceroute hostname
Description
Attempt to display
the route over which packets must travel to reach a
destination hostname. It is included here because it is
mentioned in this Objective, but Objective 3 also requires
traceroute. See the synopsis in
Objective 3 for full information.
Syntaxwhois target[@server]
fwhois target[@server]
Description
Query the whois database for target.
Such a database contains information on domain names, assigned
IP addresses, and people associated with them. In the early
days of the Internet, when domain registration was handled
solely by the Internet Network Information Center (InterNIC),
server was understood to be that of the InterNIC.
Additional registrars now exist to process domain
registrations, some of which have their own whois databases for public access.
The version of whois provided with Linux is a link
to fwhois. target is a
domain name or user handle.
server is a valid whois
server, which defaults to rs.internic.net. The
information returned includes contact information, domain
names, IP addresses, and DNS servers. Note that many web sites
are available for whois
searches as well, particularly for checking on domain name
availability.
Example$ fwhois [email protected]
Registrant:
Linux Documentation Project (LINUXDOC-DOM)
4428 NE 74th Ave.
Portland, OR 97218
US
Domain Name: LINUXDOC.ORG
Administrative Contact, Technical Contact, Zone Contact:
Account, Hostmaster (AH243-ORG)
[email protected]
Command Prompt Software
4428 NE 74th Ave.
Portland, OR 97218
US
(503)493-1611
Billing Contact:
Account, Hostmaster (AH243-ORG)
[email protected]
Command Prompt Software
4428 NE 74th Ave.
Portland, OR 97218
US
(503)493-1611
Record last updated on 15-Feb-2000
Record created on 20-Feb-1999
Database last updated on 5-Apr-2000 12:51:28 EDT
Domain servers in listed order:
NS1.OPENDOCS.ORG 209.102.107.110
NS1.INETARENA.COM 206.129.216.1
NS.UNC.EDU 152.2.21.1
|
You must have a working knowledge of
when and how to use the dig, ftp, ping, telnet, traceroute, and whois commands. Practice using
any that you are unfamiliar with by experimenting on a
working networked system.
| 
|