|
|
|
5.10 Securing Registry Keys in Windows 2000RegEdt32 allows you to set permissions on any key in the Registry. Since most of the data in the Registry belongs to system components, you must use this feature carefully; if you change permissions on a key so that the application that needs it can't get to it, you may destabilize or destroy your system. The Security Figure 5.12. Registry key Permissions dialog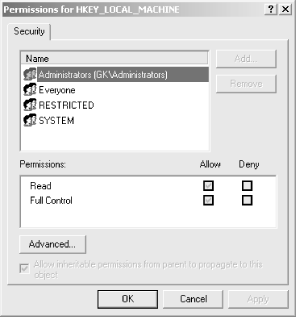
5.10.1 Setting PermissionsTo set permissions on a Registry key in Windows 2000, you have to use the Permissions tab of the Access Control Settings dialog (see Figure 5.13). This tab contains a summary of the contents of the selected key's DACL and SACL, listing each ACE individually. Figure 5.13. The Permissions tab summarizes ACEs for the current Registry key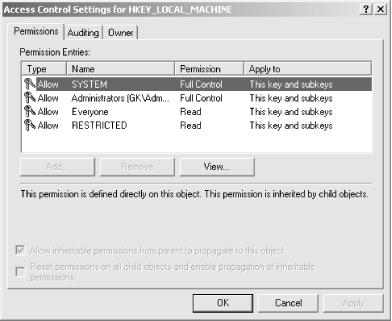 The ACLs shown in the Permission Entries list are pretty vanilla, but they still bear explanation:
5.10.1.1 Adding, removing, and changing ACE entriesYou modify ACE entries with the Add..., Remove, and View/Edit... buttons below the permission list. Let's deal with removal first, since it's the most straightforward case: select an ACE, click Remove, and it's gone (though the change isn't actually recorded in the Registry until you OK the Access Control Settings and Permissions dialogs). Adding and viewing or changing ACE entries are similar in concept and execution. When you add a new entry by clicking the Add... button, you must begin by specifying the user or group account to which the ACE applies. Once you choose a subject for the ACE, you see a dialog like the one shown in Figure 5.14. Figure 5.14. The Object tab controls the specific ACEs applied to a Registry key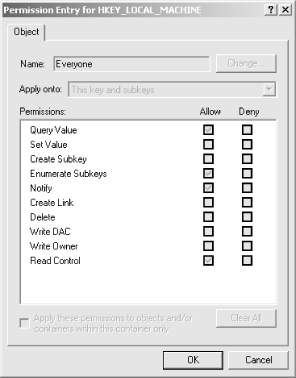
5.10.1.2 Seeing and controlling permission inheritanceMicrosoft apparently realized that the inheritance scheme for Windows 2000 permissions is a little confusing, because they took the welcome step of adding a plain-spoken description of the inheritance settings in effect for the current key. For example, Figure 5.13 says "This permission is defined directly on this object. This permission is inherited by child objects": that's a remarkably clear statement of the inheritance settings in effect for that key. The contents of the text description depend on the setting of the two checkboxes at the bottom of the dialog:
5.10.2 Auditing Registry ActivityThe Auditing tab, shown in Figure 5.15, summarizes the auditing ACL entries for the selected Registry key. Its appearance is similar to the Permissions tab shown in Figure 5.13; that's by design, since the mechanisms for reviewing and setting ACEs for auditing or object access are similar. The Auditing Entries list shows each audit ACE entry defined for the current Registry key, using a format that's almost identical to the format used for ACE entries. The primary difference is that the Type field for audit entries are either Success or Fail; this indicates whether audit log entries will be generated for successful or failed access attempts. Figure 5.15. The Auditing tab summarizes auditing entries for the current Registry key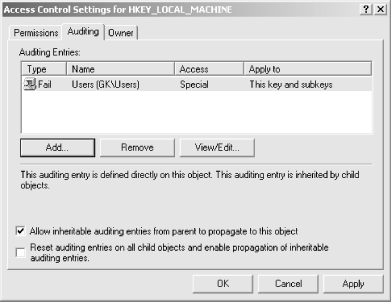 5.10.2.1 Adding, removing, and changing auditing entriesYou manage auditing entries with the Add..., Remove, and View/Edit... buttons. Like their counterparts on the Permissions tab, these buttons allow you to change the individual ACEs that make up the auditing ACL on the key you're modifying:
Figure 5.16. The Auditing Entry dialog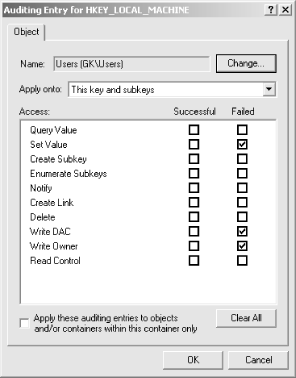 5.10.2.2 Seeing and controlling audit control inheritanceSince the Permissions and Auditing tabs are so similar, it might not be surprising that the Auditing tab contains the same plain-English[5] description of the audit settings you apply. The two checkboxes at the bottom of the tab have exactly the same effect as their counterparts on the Permissions tab; they work together to control how your audit settings are propagated to subkeys of the current key.
5.10.3 Changing Key OwnershipChanging the ownership of a particular key in Windows 2000 is pretty straightforward; that's the sole function of the Owner tab in the Access Control Settings dialog, shown in Figure 5.17. Normally, you won't change ownership of a key that belongs to the system, although in some security-related circumstances (usually dictated by a Microsoft security bulletin) you might. More often, you'll change ownership of keys used by applications you've installed to keep users from fiddling with them. The actual process of changing ownership is simple: switch to the Owner tab and select the new owner you want for the key. The Change owner to list is filled with accounts and groups that can own the current key, based on its parentage and the inheritance settings currently in force. Checking the "Replace owner on subcontainers and objects" applies the change recursively to the subkeys and values beneath the current key. Leaving it in its default unchecked state changes ownership only of the selected key and its values. Figure 5.17. The Owner tab of the Access Control Settings dialog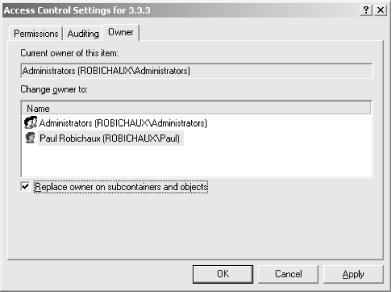 |
|
|
|