11.3 HKLM\SOFTWARE
HKLM\SOFTWARE is the motherlode of
software configuration information. Any configuration data an
application or system component needs can be stored here; settings
specific to an individual user belong in that user's
HKU\SOFTWARE key. For example, the SOFTWARE\Microsoft\Windows NT
CurrentVersion\Winlogon key stores settings that apply to the
winlogon program. These settings apply to all
users on the machine, so they belong under HKLM. On the other hand,
an individual user's choices for which tools to use to view
certain types of web content properly belong to that user, so they
should go under HKCU (e.g., Software\Netscape\Netscape
Navigator\Viewers).
11.3.1 SOFTWARE\Classes\CLSID
This key is the
root under which all the machinewide class definitions are
registered. In NT, the HKCR root key displays data from this subkey
alone. In Windows 2000, classes may also be registered under
HKCU\Software\Classes, providing for class registration on a per-user
bases. See Section 11.6.3 for
details on the format of this key's subkeys and values.
11.3.2 SOFTWARE\Microsoft
This key is the root location
for parameters and settings for all Microsoft products installed on a
machine. As you might expect, such a key covers a multitude of sins.
11.3.2.1 Microsoft\ActiveSetup
ActiveSetup
is Microsoft's name for its "new and improved"
setup system. ActiveSetup records which components have been
installed on a machine in the Installed Components subkey. Each
installed component has its own class ID subkey under Installed
Components where it can store its own settings; for example, Internet
Explorer's data is located at HKLM\SOFTWARE\Microsoft\Active
Setup\Installed Components\{89820200-ECBD-11cf-8B85-00AA005B4383}.
11.3.2.2 Microsoft\Cryptography
NT 4.0
introduced Microsoft's Cryptographic Application Programming
Interface, better known as CryptoAPI. CryptoAPI provides OS-level
services for signing, verifying, and encrypting data, as well as for
using digital certificates for access control and authentication.
Complete documentation for CryptoAPI is available online at
http://www.microsoft.com/msdn.
 The following subkeys are used for certificate storage in NT 4.0: The following subkeys are used for certificate storage in NT 4.0:
- CertificateStore
This subkey contains the store of X.509 certificates currently loaded
onto a particular machine. As new certificates arrive, CryptoAPI
applications can read and verify them, then store them here if
desired. - CertificateStore\CertificateAuxiliaryInfo
Each stored certificate can have arbitrary data associated with it.
Microsoft calls this data tags; applications may
add tags to certificates, but don't have to. This subkey is
usually empty. - CertificateStore\Certificates
The default value of this subkey contains the number of certificates
as a REG_SZ, plus one named value for each certificate. For example,
if three certificates are present, they are stored in values named
"1," "2," and "3," and the
default value contains "3." Each certificate's
value contents consist of a binary chunk of data that actually
contains the certificate itself.
In Windows 2000, certificates are stored and managed through the use
of the MMC Certificates snap-in. There are a number of subkeys
throughout the Registry that store certificates, and they're
certainly not limited to the HKLM root key. Indeed, HKCU contains
subkeys that hold certificates for users, while certificates are also
found in HKU\Default. And yes, the HKLM root key contains certificate
stores, such as HKLM\Software\Microsoft\EnterpriseCertificates and
HKLM\Software\Microsoft\Cryptography\Services\PolicyAgent\SystemCertificates.
In general, the certificate storage structure in the Windows 2000
Registry begin with a subkey such as SystemCertificates or
EnterpriseCertificates. Beneath this subkey appears a list subkeys
that correspond to a certificate type. Here are the four most
prevalent:
- CA
This subkey contains X.509 certificates, certificate revocation
lists, and certificate trust lists for Certificate Authorities. CAs
issue certificates to individual users and services. - My
Individual certificates are stored here. - Root
Certificates, certificate revocation lists, and certificate trust
lists associated with root authorities (that is, authorities at the
top of the certificate trust chain) are found under this subkey. - Trust
This subkey contains certificates, revocation lists, and trust lists
that help determine trust.
Beneath these certificate types are three subkeys, namely
Certificates, CRLs (certificate revocation lists), and CTLs
(certificate trust lists). The values beneath these subkeys contain
binary data, forming lists of certificates, revocation lists and
trust lists, respectively.
11.3.2.3 Microsoft\ NtBackup
The bundled Windows NT backup tool stores
its settings here. Interestingly, this key is remapped by
HKLM\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\IniFileMapping\Ntbackup.ini, meaning that the
backup program (bless its ancient little heart) thinks it's
using an INI file to store its settings in.
11.3.2.4 Microsoft\RAS
The
Dial-Up Networking service was originally
known as RAS. Sometimes Microsoft calls it RAS, sometimes DUN; in
this case, its Registry settings all have "RAS" in the
name somewhere. The values in this key control the Remote Access
Service, which clients can use to dial into a Windows 2000 or NT
machine.
- CurrentVersion
This subkey looks very much like the CurrentVersion\Network Cards
keys you'll meet in the section by the same name. That's
not surprising, since RAS is really just a virtual NIC.
CurrentVersion's values specify the setup info file name
(Infname), major and minor software versions, and the path where RAS
parts are stored (PathName). In addition, the CurrentVersion\NetRules
subkey specifies the rest of the information gathered when RAS was
first installed. - Protocols
This subkey contains a set of REG_DWORD flags that govern which
protocols are selected and which may be used. For example, the f
TcpIpSelected and f TcpIpAllowed flags indicate whether the server
supports TCP/IP RAS connections or not.
Each installed RAS protocol has its own subkey; for example,
TCP/IP-specific settings are stored in Microsoft\RAS\Protocols\IP.
These subkeys contain values and flags specific to the protocol.
-
TAPI DEVICES
This subkey holds a list of any Telephony API (TAPI)-compliant
devices known to the RAS service, including any Unimodem
devices.
11.3.3 SOFTWARE\Microsoft\Windows NT
This subkey contains configuration
settings specific to Windows 2000 (on Windows 2000 machines) or NT
(on NT machines); this key doesn't include settings for the
shell or Explorer. The CurrentVersion subkey contains a number of
interesting pieces of data, as well as some subkeys that merit their
own mentions:
- RegisteredOwner and RegisteredOrganization
These REG_SZ values store whatever values you entered into the name
and company fields of the system's installation dialogs. You
can freely change them if need be. - CurrentVersion and CurrentBuildNumber
Together these two REG_SZ values identify what core version of
Windows 2000/NT you're running. A stock Windows 2000
installation has a version of "5.0" and a build number of
"2195"; later versions will obviously have different
values. - SystemRoot
This value points to the system directory. If you ever need to
migrate your Windows 2000 or NT installation to a different volume,
be sure to update this as part of the process. - SourcePath
This REG_SZ points to the source from which the operating system was
originally installed. For example, on my machine this value contains
a path to the CD-ROM, "G:\i386". - ProductId
This string holds the Microsoft "product ID," which is
nothing more than a magic number combined with your CD key. A typical
product ID looks like "64366-492-0966186-35833". - CSDVersion
This value indicates what service pack, if any, is installed. The
boot loader uses this (along with CurrentVersion and
CurrentBuildNumber) to display the blue-screen boot-time message that
tells you what you're booting.
11.3.3.1 CurrentVersion\
AeDebug
This subkey tells the system what debugging application to use (if
any) when a program crashes.
- Debugger
The program to run when an application crashes. The value may include
the full path and any arguments (for example, the default debugger,
Dr. Watson, appears as drwtsn32 -p %ld -e %ld -g
). - Auto
REG_SZ specifying whether the debugger should just be run
("1") or whether the user should be prompted to choose
between starting the debugger and killing off the errant app
("0", the default). - UserDebuggerHotKey
REG_DWORD that, when set, specifies a key code that instantly starts
the debugger when pressed. Leave this alone.
11.3.3.2 Multimedia driver stuff
The installed list of multimedia device
drivers is stored in three subkeys of CurrentVersion: Drivers32,
drivers.desc (or DriverDesc), and DriverList. They're pretty
self-explanatory; each device class has a mapping that specifies what
DLL handles its requests and what its human-readable name is.
11.3.3.3 CurrentVersion\Network Cards
This
subkey contains one entry for each installed network adapter card or
wrapper. For example, a machine with one network card and Dial-Up
Networking installed has two entries: one for the NIC and one for
DUN. The first entry is stored in a subkey named "1" (or
CurrentVersion\Network Cards\1 if you prefer), and subsequent cards
count up from there. These keys each have several values, but the
most important ones are ServiceName (which specifies which driver
runs the card) and Title (which determines the name that appears in
the Network control panel).
Each network adapter subkey can in turn have a subkey named NetRules.
This key contains values that specify what kind of adapter it is
(type), what setup information file was used to install it (InfName),
and what kind of device it actually is (class and block).
11.3.3.4 CurrentVersion\
ProfileList
The list of cached profiles on a particular machine lives here. Each
profile has a subkey whose name is its SID ; these subkeys contain a
path that points to the actual hive containing the profile
(ProfileImagePath), some flags that the system uses to control
profile loading (Flags and State), and a second copy of the SID that
owns the profile (Sid).
11.3.3.5 CurrentVersion\
Shutdown
There are two interesting values stored under this key: LogoffSetting
and ShutdownSetting. Both are DWORD values that may range from 0-3.
They control what button is selected by default in the Logoff and
Shutdown dialogs; you can preset the choice you want to use as a
default by adjusting their contents. Table 11.1
lists the available values.
Table 11.1. CurrentVersion\Shutdown Controls the Default Logoff and Shutdown Buttons
|
0
|
Make the "Logoff" button the default
|
|
1
|
Make the "Shutdown" button the default
|
|
2
|
Make the "Shutdown and Restart" button the default
|
|
3
|
Make the "Shutdown and Power Off" button the default;
ignored unless the computer has power-management support
|
11.3.3.6 CurrentVersion\Winlogon
The Winlogon service provides a graphical interface that allows you
to log onto or off of the console of a Windows 2000 or NT computer.
The values under the Winlogon subkey let you change some aspects of
how the logon process works.
 |
Most of these values are here for you to customize. The Group Policy
snap-in for Windows 2000 machines and the System Policy Editor for
Windows NT machines provide an easy way to set these values to meet
your needs, even for many computers. See Chapter 6, and Chapter 7 for details.
|
|
- AutoAdminLogon
Signals whether the computer should automatically log on with a
stored account name and password. When this REG_SZ is set to 1, the
values of DefaultUserName, DefaultDomainName, and DefaultPassword are
used to attempt a logon. This value must be manually added. - AutoRestartShell
REG_DWORD that controls whether Explorer (or whatever other shell
program's specified) should be restarted if it crashes. The
default, 0x01, means yes. 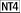 DebugServerCommand DebugServerCommandMicrosoft describes this as a command used for internal debugging of
Winlogon at Microsoft. Its default value is "no"; I have
no idea what other values might mean. If you know, please tell me. - DefaultDomainName
Winlogon stores the name of the domain (or
machine) that hosted the last successful logon here. - DefaultPassword
When AutoAdminLogon is set to 1, this password (which must be the
password for the account given in DefaultUserName) is used in the
logon attempt. - DefaultUserName
Winlogon stores the name of the last account
that successfully logged on in this value. You may change it and set
the AutoAdminLogon value to force an automatic logon to a particular
account. - DeleteRoamingCache
When this REG_DWORD value is set to 1, cached copies of roaming
profiles are deleted when each user logs off. You must add this value
manually. - DontDisplayLastUserName
Windows 2000/NT normally displays the name of the last account to log
on in the Welcome dialog. Set this REG_SZ value to 1 to keep this
space blank, or
(the default) to allow the last account to be displayed. - LegalNoticeCaption
Windows 2000/NT can display a warning dialog immediately after the
logon dialog is dismissed; this makes it possible for you to display
a warning message, as recommended by the Computer Emergency Response
Team, to warn intruders that they are in fact intruding. The system
uses the REG_SZ value you put in LegalNoticeCaption to title the
warning dialog. By default in Windows 2000 and NT 4.0, this value
exists but is empty. - LegalNoticeText
The warning text displayed in the post-logon warning dialog comes
from the LegalNoticeText value, which is also blank by default. - ParseAutoexec
REG_SZ that specifies whether autoexec.bat
should be parsed at logon time or not. If the value is set
to 1, autoexec.bat is parsed when you log on,
and the autoexec.bat path statement is appended
to the system path. 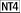 PowerdownAfterShutdown PowerdownAfterShutdownREG_SZ that controls whether the system attempts to power down the
computer when it's shut down.
means no; 1 means yes. This value has no effect on machines without
power-management support. - ProfileDlgTimeOut
If a user logs in but can't get a copy of his current logon
profile, the system displays a dialog asking what the user wants done
to fix the problem. This REG_DWORD value sets the timeout (in
seconds, from 0-0xFFFFFFFF in Windows 2000; 0-600 in NT) after which
any user profile dialog boxes are automatically dismissed. -
ReportBootOk
When Windows 2000 or NT boots, it saves the boot configuration as the
"last known good" control set. Ordinarily, this REG_SZ is
set to 1, which tells the system to update the control set
automatically when booting finishes. If this REG_SZ value is set to
0, the system won't automatically update the last known good
set. Another program, such as Bootok.exe or
Bootvrfy.exe must be used. This value must be
"0" if you supply alternate values in the
BootVerification or BootVerificationProgram keys. - RunLogonScriptSync
Specifies whether logon scripts should be run synchronously (so the
desktop doesn't appear until the script completes) or
asynchronously (so the script runs while the desktop is being
activated). This is a REG_SZ; set it to 1 to force the script to run
synchronously. - Shell
This value tells Windows 2000/NT what program to run as the system
shell. By default, explorer.exe is the preferred
shell. Setting up a Zero-Administration Windows (ZAW) workstation
usually sets the preferred share to
iexplore.exe. You may change it manually, but
doing so may have unpredictable results. - ShutdownWithoutLogon
As an administrator, you may choose whether or not to allow users to
shut down their workstations or servers without being logged in. A
REG_SZ value of 1 in this value adds or enables a Shutdown button to
the standard logon dialog, while a value of
removes or disables it. By default, this button is on for Windows
2000 Professional and NTW 4.0, and off for Windows 2000 Server and
NTS 4.0. - SlowLinkDetectEnabled
When set to on (the default), Winlogon automatically detects slow
network connections and flags them as such. When off, no such
detection occurs. - SlowLinkTimeOut
This REG_DWORD sets the timeout value, in milliseconds, after which a
link is marked slow when SlowLinkDetectEnabled is on. 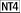 System System This value specifies which programs are trusted to run in the system
context. Changing it may open a security hole, since untrusted
programs can run with high privileges. The default is
lsass.exe; don't change it. In NT 4.0
pre-SP3, the default also includes spoolss.exe. - Taskman
Specifies the path to an executable to be used for the system task
manager. On Windows 2000 machines, this value is
taskmgr.exe by default. - Userinit
This value specifies which programs should be started automatically
when a user successfully logs on. The default value in Windows 2000
is userinit, which specifies that the shell
named in Shell should be run. In Windows NT,
nddeagnt.exe is also added as a default. This
then starts the NetDDE service process. - VmApplet
This value determines which program should be run to adjust the
virtual memory configuration. The default contents of this value are
rundll32 shell32, Control_RunDLL, "sysdm.cpl".
|