 | Chapter 6 Cryptography |  |
To understand how some modern encryption programs work, consider the raison d'�tre for the birth of computers in the first place: the Enigma encryption device, used by the Germans during the Second World War. A photograph of an Enigma encryption device appears in Figure 6.2.

Enigma was developed in the early 1900s in Germany by Arthur Scherbius and used throughout World War II. The Enigma encryption machine, illustrated in the photo, consisted of a battery, a push-button for every letter of the alphabet, a light for every letter of the alphabet, and a set of turnable discs called rotors. The Enigma machine was similar to a child's toy: pressing a button lit a different light. If you turned one of the rotors, the correspondence between buttons and lights changed.
The rotors were crucial to the machine's cryptographic abilities. Each rotor on the Enigma machine was similar to a sandwich, with 52 metal contacts on each side. Inside the rotors, shown schematically in Figure 6.3, were 52 wires, each wire connecting a pair of contacts, one on either side of the rotor. Instead of directly connecting the contacts on one side with those on the other side, the wires scrambled the order, so that, for example, contact #1 on the left might be connected with contact #15 on the right, and so on.
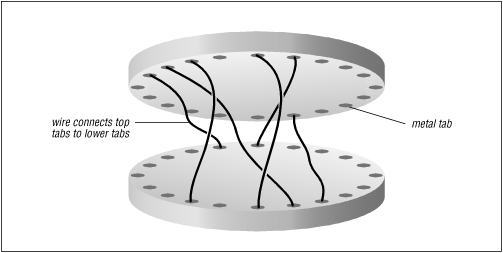
Enigma placed three of these rotors side by side. At the end of the row of rotors was a reflector, which sent the electrical signal back through the machine for a second pass. (Four rotors were used near the end of the war.) Half of the 52 contacts were connected with a push-button and the battery; the other half were connected with the lights. Each button closed a circuit, causing a light to brighten; however, precisely which light brightened depended on the positioning of the three rotors and the reflector.
To encrypt or decrypt a message, a German code clerk would set the rotors to a specific starting position - the key. For each letter, the code clerk would then press the button, write down which letter lit, and then advance the rotors. Because the rotors were advanced after every letter, the same letter appearing twice in the plaintext would usually be encrypted to two different letters in the ciphertext. Enigma was thus a substitution cipher with a different set of substitutions for each letter in the message; these kinds of ciphers are called polyalphabetic ciphers. The letter Z was used to represent a space; numbers were spelled out. Breaking an encrypted message without knowing the starting rotor position was a much more difficult task.