 |  |

WARNING: Unless you are completely comfortable taking the registry editing leap, we strongly recommend that you use the System Policy Editor to make agent configuration changes. Incorrect settings in the registry can result in serious system problems. Consider yourself warned.The Windows System Policy Editor comes with the Windows 95/98 Resource Kit, and must be installed before you can configure the SNMP agent. The first time you run the System Policy Editor it will ask you for an .adm file. Select C:\WINDOWS\INF \ADMIN.ADM as this file. Select "File
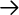 Open Registry," then double-click the Local
Computer icon. In the Policies tab, click down the plus signs until
you reach Network and then SNMP. This should leave you with four SNMP
agent configuration items. Figure 7-1 shows what
your window should look like. To enable an option, place a check next
to it. When you are finished, click "OK," then
"File
Open Registry," then double-click the Local
Computer icon. In the Policies tab, click down the plus signs until
you reach Network and then SNMP. This should leave you with four SNMP
agent configuration items. Figure 7-1 shows what
your window should look like. To enable an option, place a check next
to it. When you are finished, click "OK," then
"File  Save" at the main screen. If you don't
follow these steps, your configuration won't be saved to the
registry.
Save" at the main screen. If you don't
follow these steps, your configuration won't be saved to the
registry.
 Save" at the main
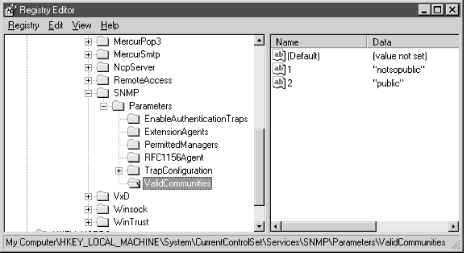
menu of the System Policy Editor. Figure 7-2 shows
what the `entries look like in the Registry Editor, after
you've used the Policy Editor to set them.
Save" at the main
menu of the System Policy Editor. Figure 7-2 shows
what the `entries look like in the Registry Editor, after
you've used the Policy Editor to set them.
sysServices OBJECT-TYPE
SYNTAX INTEGER (0..127)
ACCESS read-only
STATUS mandatory
DESCRIPTION
"A value which indicates the set of services that this entity
primarily offers.
The value is a sum. This sum initially takes the value zero.
Then, for each layer, L, in the range 1 through 7, that this node
performs transactions for, 2 raised to (L - 1) is added to the sum.
For example, a node which performs primarily routing functions
would have a value of 4 (2^(3-1)). In contrast, a node which is a
host offering application services would have a value of 72
(2^(4-1) + 2^(7-1)). Note that in the context of the Internet
suite of protocols, values should be calculated accordingly:
layer functionality
1 physical (e.g., repeaters)
2 datalink/subnetwork (e.g., bridges)
3 internet (e.g., IP gateways)
4 end-to-end (e.g., IP hosts)
7 applications (e.g., mail relays)
For systems including OSI protocols, layers 5 and 6 may also
be counted."
::= { system 7 }$ /sbin/init.d/SnmpMaster stop $ /sbin/init.d/SnmpMaster start
The simplest configuration is to edit the file and place more reasonable community names in the first two lines. We can't say it too much: community names are essentially passwords. Use the same rules for picking community names that you would for choosing the root password. You should always set the destination trap host (trap-dest) to the IP address of the host that will receive the trap. The next example configures several different community names:get-community-name: public set-community-name: private trap-dest: 127.0.0.1 contact: B.Gates location: 12 Pyramid - Egypt
We have created two get (read-only) communities and three set (read-write) communities. These communities can be used as you see fit. (In real life, we would have chosen more obscure names.) For example, you might give your operations group in New York public community access and your operations group in Atlanta media community access. The remaining set communities can further be subdivided among various administrators and other staff who need read-write access.get-community-name: public get-community-name: media set-community-name: hushed set-community-name: veryprivate set-community-name: shhhh
You can also configure the agent to restrict access to MIB subtrees based on IP addresses. The next example allows any host to get any object under iso.org.dod.internet.mgmt.mib-2, except for objects in the interfaces subtree. The minus sign (-) in front of interfaces instructs the agent to disallow access to this subtree.get-community-name comname IP: 10.123.56.25 10.123.46.101 set-community-name private IP: 10.123.56.25
The final example sets up multiple community names for both sets and gets. An administrator who is located at host 10.123.46.25 and knows the admin community string has read access to the entire MIB tree; with the adminset community string, he has write access to the entire tree. Someone with the operator community string can sit anywhere and access everything in mib-2 except for the interfaces subtree, but must be sitting at his desk (10.123.56.101) to issue sets and is not allowed to set anything in the mib-2 subtree.get-community-name public VIEW: mib-2 -interfaces
get-community-name operator VIEW: mib-2 -interfaces get-community-name admin IP: 10.123.56.25 set-community-name operset IP: 10.123.46.101 VIEW: -mib-2 set-community-name adminset IP: 10.123.56.25
One common option is - -prefix=PATH. This specifies an alternate installation directory. By default, Net-SNMP will install in /usr/local/bin, /usr/local/man, etc. We'll be running configure without any options, which means our Net-SNMP build will have default values assigned for various options. For example, the agent binary will be placed in /usr/local/sbin. Run the following command to begin the configuration process:ucd-snmp-4.2/> ./configure --help
You will see various messages about what features configure is looking for and whether or not they're found. After running for a while, configure will ask for some basic SNMP information:ucd-snmp-4.2/> ./configure
************** Configuration Section **************
You are about to be prompted by a series of questions. Answer
them carefully, as they determine how the snmp agent and related
applications are to function.
After the configure script finishes, you can browse the newly
created config.h file for further - less important - parameters to
modify. Be careful if you re-run configure though since config.h will
be over written.
-Press return to continue-disabling above prompt for future runs... yes
checking System Contact Information...
*** System Contact Information:
Describes who should be contacted about the host the agent is
running on. This information is available in the MIB-II tree. This
can also be over-ridden using the "syscontact" syntax in the agent's
configuration files.
System Contact Information (root@): [email protected]
setting System Contact Information to... [email protected]
checking System Location... *** System Location:
Describes the location of the system. This information is
available in the MIB-II tree. This can also be over-ridden using the
"syslocation" syntax in the agent's configuration files.
System Location (Unknown): FTP Server #1, O'Reilly Data Center
setting System Location to... FTP Server #1, O'Reilly Data Center
checking Location to write logfile... *** Logfile location:
Enter the default location for the snmpd agent to dump
information & errors to. If not defined (enter the keyword "none"
at the prompt below) the agent will use stdout and stderr instead.
(Note: This value can be over-ridden using command line options.)
Location to write logfile (/var/log/snmpd.log):
setting Location to write logfile to... /var/log/snmpd.log
*** snmpd persistent storage location:
Enter a directory for the snmp library to store persistent
data in the form of a configuration file.
Location to write persistent information (/var/ucd-snmp):
setting Location to write persistent information to... /var/ucd-snmp
updating cache ./config.cache
creating ./config.status
creating Makefile
creating MakefileMakefile
creating snmplib/Makefile
creating agent/Makefile
creating apps/Makefile
creating apps/snmpnetstat/Makefile
creating agent/mibgroup/Makefile
creating agent/dlmods/Makefile
creating local/Makefile
creating testing/Makefile
creating man/Makefile
creating ov/Makefile
creating mibs/Makefile
creating config.h/* default list of mibs to load */
#define DEFAULT_MIBS "IP-MIB:IF-MIB:TCP-MIB:UDP-MIB:SNMPv2-MIB: \
RFC1213-MIB:UCD-SNMP-MIB:SNMPv2-PARTY-MIB:SNMPv2-M2M-MIB: \
SNMP-VIEW-BASED-ACM-MIB"
/* default location to look for mibs to load using the above tokens
and/or those in the MIBS environment variable */
#define DEFAULT_MIBDIRS "/usr/local/share/snmp/mibs"
/* LOGFILE: If defined it closes stdout/err/in and opens this in out/err's
place. (stdin is closed so that sh scripts won't wait for it) */
#define LOGFILE "/var/log/snmpd.log"
/* default system contact */
#define SYS_CONTACT "[email protected]"
/* system location */
#define SYS_LOC "FTP Server #1, O'Reilly Data Center"syslocation "O'Reilly Data Center"
syscontact [email protected]
rwcommunity private
rocommunity public
authtrapenable 1
trapcommunity trapsRus
trapsink nmshost.oreilly.com
trap2sink nmshost.oreilly.comIf you take this route, you should certainly look at the EXAMPLE.conf file in the directory in which you built Net-SNMP. You can modify this file and install it in the appropriate location (either ~/.snmp/snmpd.conf or /usr/local/share/snmp/snmpd.conf ), or you can take ideas from it and use them in your own configuration. It includes some particularly clever tricks that we'll discuss in Chapter 11, "Extensible SNMP Agents" but that are well beyond the simple configuration we're discussing here.rwcommunity private 10.0.15.0
Comment lines begin with a # character. The first parameter sets the read-only community to public. The read-write community is defined to be veryprivate. The two IP addresses following the read-write community string are an access list that tells the agent to allow set operations from localhost (127.0.0.1) and 10.123.56.25 only. Always use an access list if possible; without this security feature, any host can execute set operations. Note that there is a space between the two addresses, not a Tab character. The third option tells the agent where to send traps; in this case, to localhost (127.0.0.1). The agent sends authentication-failure traps by default, and we strongly recommend using them. If you don't want authentication-failure traps, include the following line in your configuration file:community public read-only community veryprivate read-write 127.0.0.1 10.123.56.25 community traps 127.0.0.1
no_authen_traps
This monitor sends a trap to the NMS, defined earlier as community traps 127.0.0.1, when the sendmail process dies. The agent then executes /etc/init.d/sendmail start to restart the process. The general form of this command is:watch process procAlive 'sendmail' 1 0x100 60 'Watch Sendmail' '/etc/init.d/sendmail start'
The procname parameter is a regular expression that SystemEDGE uses to select the processes that it is monitoring; in this case, we're watching processes with the name sendmail. Each entry in the process-monitoring table must have a unique index; in this example, we used the value 1. We could have picked any integer, as long as that integer was not already in use in the table. The flag parameter is a hexadecimal[28] flag that changes the behavior of the monitor. We specified a flag of 0x100, which tells the monitor that the process it's watching spawns child processes; this flag ensures that SystemEDGE will take action only when the parent sendmail process dies, not when any of the children die. The use of process-monitor flags is beyond the scope of this chapter; see the manual that comes with SystemEDGE for more information. The interv parameter specifies how often (in seconds) the agent checks the process's status. We have set the interval to 60 seconds. The description parameter contains information about the process being monitored; it can be up to 128 characters in length. It is a good idea to use a description that indicates what is being monitored, since the agent stores this value in the monitor table for retrieval by an NMS and includes it in the variable bindings when a trap is sent. The final parameter is the action the monitor will take when the process dies; we chose to restart the daemon.watch process procAlive 'procname' index flags interv 'description' 'action'
[28]Generally speaking, there are several ways to represent hexadecimal numbers. SystemEDGE uses the notion of a number prefixed with 0x, which should be familiar to C and Perl programmers.SystemEDGE can be extended by using plug-ins. These plug-ins manage and monitor applications such as Apache (web server), Exchange (Microsoft mail), and Oracle (database), to name a few. A "top processes" plug-in named topprocs comes with every distribution. The following statement tells SystemEDGE to load this plug-in for 64-bit Solaris (this statement is similar for NT and other Unix platforms):
The folks at Concord have taken great care to add useful comments to the sysedge.cf file. The comments are often all you need to configure the agent.sysedge_plugin /opt/EMPsysedge/plugins/topprocs/topprocs-sol64bit.so
[29]There are some exceptions to this rule, such as the PIX firewalls. These exceptions usually mean that the product is made by a company that Cisco acquired.To configure the SNMP parameters, you must be in enable mode. You can use the following commands to see what traps are available:
The question mark tells the router to respond with the possible completions for the command you're typing. You can use this feature throughout the entire command-line interface. If the part of the command you have already typed has a syntax error, the router will give you the "Unrecognized command" message when you type the question mark. <cr> tells you that you can exit without configuring the command (snmp-server enable traps in this case) by typing a carriage return.router> enable Password: mypassword router# config terminal router(config)#snmp-server enable traps ? bgp Enable BGP state change traps envmon Enable SNMP environmental monitor traps frame-relay Enable SNMP frame-relay traps isdn Enable SNMP isdn traps <cr>
Most of these commands set parameters with which you should be familiar by now. We define two communities, public and private, with read-only (RO) and read-write (RW) permissions, respectively. snmp-server trap-authentication turns on authentication-failure traps. The command snmp-server host 10.123.135.25 public configures the destination to which traps should be sent. The IP address is set to the address of our NMS. The community string public will be included in the traps.router(config)#snmp-server community private RW router(config)#snmp-server community public RO router(config)#snmp-server trap-authentication router(config)#snmp-server location Delta Building - 1st Floor router(config)#snmp-server contact J Jones router(config)#snmp-server host 10.123.135.25 public
Configuring the trap source is useful because routers, by definition, have multiple interfaces. This command allows you to send all your traps out through a particular interface. There may be times when you want to send only certain traps to your NMS. The next item sends only environmental monitor traps to the specified host, 172.16.52.25 (the envmon option is not available on all Cisco devices):router(config)#snmp-server trap-source VLAN1
One of the most frightening SNMP sets is the Cisco shutdown, which lets you shut down the router from the NMS. The good news is that you have to include a switch in the configuration before the router will respond to shutdown commands. Issuing the following command disables shutdowns:router(config)#snmp-server host 172.16.52.25 public envmon
To receive traps about authentication failures (something trying to poll your device with the wrong community name) add the following line:router(config)#no snmp-server system-shutdown
The final advanced configuration parameter is an access list. The first line sets up access list 15. It states that the IP address 10.123.56.25 is permitted to access the agent. The second line says that anyone that passes access list 15 (i.e., a host with IP address 10.123.56.25) and gives the community name notsopublic has read-only (RO) access to the agent. Access lists are a very powerful tool for controlling access to your network. They're beyond the scope of this book, but if you're not familiar with them, you should be.router(config)#snmp-server trap-authentication
That's it! You now have a working SNMP configuration for your Cisco router.router(config)#access-list 15 permit 10.123.56.25 router(config)#snmp-server community notsopublic RO 15
------- SNMP ------------------------------------------------------------
1- Access Control 1
2- Access Control 2
3- Access Control 3
4- Access Control 4
5- Trap Receiver 1
6- Trap Receiver 2
7- Trap Receiver 3
8- Trap Receiver 4
9- System
10- Summary
?- Help
<ENTER> Redisplay Menu
<ESC> Return To Previous Menu
>------- Access Control 1 ------------------------------------------------
Access Control Summary
# Community Access NMS IP
-----------------------------------------------------------------
1 public Read 10.123.56.25
2 private Write 10.123.56.25
3 public2 Disabled 0.0.0.0
4 private2 Disabled 0.0.0.0
1- Community : public
2- Access Type : Read
3- NMS IP Address : 10.123.56.25
4- Accept Changes :
?- Help
<ENTER> Redisplay Menu
<ESC> Return To Previous Menu
> ------- Trap Receiver 1 -------------------------------------------------
Trap Receiver Summary
# Community Generation Authentication Receiver NMS IP
-----------------------------------------------------------------------
1 public Enabled Enabled 10.123.56.25
2 public Enabled Enabled 0.0.0.0
3 public Enabled Enabled 0.0.0.0
4 public Enabled Enabled 0.0.0.0
1- Trap Community Name : public
2- Trap Generation : Enabled
3- Authentication Traps: Enabled
4- Receiver NMS IP : 10.123.56.25
5- Accept Changes :
?- Help
<ENTER> Redisplay Menu
<ESC> Return To Previous Menu
>------- System ----------------------------------------------------------
1- sysName : ups1.ora.com
2- sysContact : Douglas Mauro
3- sysLocation : Apache Hilo Deck
4- Accept Changes :
?- Help
<ENTER> Redisplay Menu
<ESC> Return To Previous Menu
>-------------------------------------------------------------------------
SNMP Configuration Summary
sysName : ups1.ora.com
sysLocation : Apache Hilo Deck
sysContact : Douglas Mauro
Access Control Summary
# Community Access NMS IP
-----------------------------------------------------------------
1 public Read 10.123.56.25
2 private Write 10.123.56.25
3 public2 Disabled 0.0.0.0
4 private2 Disabled 0.0.0.0
Trap Receiver Summary
# Community Generation Authentication Receiver NMS IP
--------------------------------------------------------
1 public Enabled Enabled 10.123.56.25
2 public Enabled Enabled 0.0.0.0
3 public Enabled Enabled 0.0.0.0
4 public Enabled Enabled 0.0.0.0
Press <ENTER> to continue...
Copyright © 2002 O'Reilly & Associates. All rights reserved.