| [ Team LiB ] |
|
11.3 Administering Isolated StorageThere are two aspects to the administration of isolated storage:
In the following sections, we discuss the administration of isolated storage, beginning with the configuration of security policy. 11.3.1 Configuring Security PolicyYou can use both the .NET Framework Configuration tool (Mscorcfg.msc) and the Code Access Security Policy tool (Caspol.exe) to administer security policy to grant access to isolated storage. We discussed the general use of Mscorcfg.exe and Caspol.exe in Chapter 9. In the following sections, we describe how to use Mscorcfg.exe and Caspol.exe specifically to control access to isolated storage. 11.3.1.1 Granting isolated storage permissions with Mscorcfg.mscTo grant code access to isolated storage, you must create a named permission set that grants its members the IsolateStorageFilePermission class, and you must assign this permission set to a code group. To create a permission set containing IsolateStorageFilePermission, you should follow the process we described in Section 11.1.1.1 of Chapter 9. Figure 11-3 shows the dialog box through which you select the permissions to add to the new permission set. The Isolated Storage File entry (highlighted in the diagram) represents the IsolateStorageFilePermission class. Figure 11-3. Selecting IsolatedStorageFilePermission graphically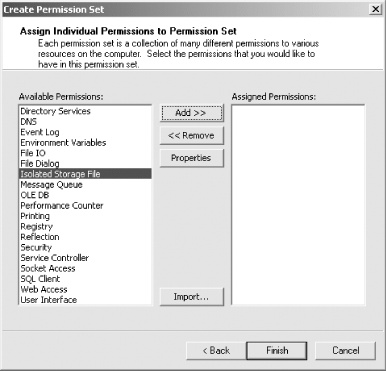 When you press the Add >> button to include the IsolateStorageFilePermission in your permission set, the dialog box shown in Figure 11-4 appears and allows you to configure the specific level of isolated storage access to grant. Figure 11-4. Configuring IsolatedStorageFilePermission graphically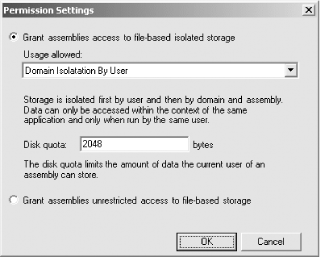 You can grant unrestricted access to isolated storage by pressing the bottom radio button, or grant a specific level of access by pressing the top radio button and choosing the desired level from the Usage Allowed drop-down list. The configuration maps to the values of the IsolatedStorageContainment enumeration, which we discussed in Section 11.2.1 earlier in this chapter. 11.3.1.2 Granting isolated storage permissions with Caspol.exeIn Chapter 9, we explained how to use Caspol.exe to administer code-access security. To create a named permission set that grants access to isolated storage, you must generate an XML file that contains the description of a System.Security.NamedPermissionSet object containing a configured IsolateStorageFilePermission object. Because of the complexity of the XML description, we recommend that you don't try to create these XML files manually; you should create the permission set programmatically, and then write its XML description to a file, as demonstrated in Example 11-4: Example 11-4. Programmatically creating an XML description of a permission set# C#
using System;
using System.IO;
using System.Security;
using System.Security.Permissions;
public class WritePermSet {
public static void Main( ) {
// Create an empty NamedPermissionSet
NamedPermissionSet nps =
new NamedPermissionSet("IsoTestSet",PermissionState.None);
// Create an IsolatedStorageFilePermission and add it to the
// NamedPermissionSet
IsolatedStorageFilePermission p =
new IsolatedStorageFilePermission(PermissionState.None);
p.UsageAllowed = IsolatedStorageContainment.DomainIsolationByUser;
p.UserQuota = 2048;
nps.AddPermission(p);
// Write the NamedPermissionSet to a file
StreamWriter sw = new StreamWriter("IsoTestSet.xml");
sw.Write(nps.ToString( ));
sw.Close( );
}
}
# Visual Basic .NET
Imports System
Imports System.IO
Imports System.Security
Imports System.Security.Permissions
Public Class WritePermSet
Public Shared Sub Main( )
' Create an empty NamedPermissionSet
Dim nps As NamedPermissionSet = _
New NamedPermissionSet("IsoTestSet",PermissionState.None)
' Create an IsolatedStorageFilePermission and add it to the
' NamedPermissionSet
Dim p As IsolatedStorageFilePermission = _
New IsolatedStorageFilePermission(PermissionState.None)
p.UsageAllowed = IsolatedStorageContainment.DomainIsolationByUser
p.UserQuota = 2048
nps.AddPermission(p)
' Write the NamedPermissionSet to a file
Dim sw As StreamWriter = new StreamWriter("IsoTestSet.xml")
sw.Write(nps.ToString( ))
sw.Close( )
End Sub
End Class
Running this utility produces a file named IsoTestSet.xml that contains the following XML: <PermissionSet class="System.Security.NamedPermissionSet"
version="1"
Name="IsoTestSet">
<IPermission class="System.Security.Permissions.IsolatedStorageFilePermission,
mscorlib, Version=1.0.5000.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"
version="1"
Allowed="DomainIsolationByUser"
UserQuota="2048"/>
</PermissionSet>
You can use the IsoTestSet.xml file to create a new permission set in the machine policy level using the following command: caspol -machine -addpset IsoTestSet.xml 11.3.2 Managing Isolated Storage StoresThe Isolated Storage tool (Storeadm.exe) is a command-line tool that comes with the .NET Framework SDK and is located in the /bin subdirectory of the SDK installation directory. Storeadm.exe allows you to list or remove the stores of the current user; no tool lets you manage isolated storage for all users, and you must manage the user's roaming and nonroaming stores independently. To list the nonroaming stores of the current user, use the command storeadm /list. Specifying the /roaming flag lists the roaming stores—for example, storeadm /list /roaming. Either of these commands displays a list of stores but not content, similar to that shown here. We have abbreviated the StrongName.Key and Publisher.X509Certificate elements in the interest of brevity: Microsoft (R) .NET Framework Store Admin 1.0.3705.0 Copyright (C) Microsoft Corporation 1998-2001. All rights reserved. Record #1 [Assembly] <StrongName version="1" Key="002400000480000094000000060200000024000052534131 00040000010001005308669520E62E2E1F08F07B0D5DA0B33C0F82AC093C54E26 852080E8C5B7" Name=" SomeOtherApp" Version="1.5.0.0"/> Size : 0 Record #2 [Domain] <System.Security.Policy.Url version="1"> <Url>file://C:/Development/projects</Url> </System.Security.Policy.Url> [Assembly] <System.Security.Policy.Publisher version="1"> <X509v3Certificate>308201713082011BA0030201020210E5D7C7E57FD9B9B347A7EE AC3221100A39899EB866979DBBB6430F5A52A024FC7FCEE9</X509v3Certificate> </System.Security.Policy.Publisher> Size : 0 The example output contains information about two stores: Record #1 and Record #2 (which we have highlighted in boldface). Record #1 represents a store isolated by user and assembly; the assembly's StrongName evidence identifies the creating code. Record #2 represents a store isolated by user, assembly, and application domain; the application domain's Url evidence and the assembly's Publisher evidence identify the creating code. Storeadm.exe also allows you to remove stores for the current user. However, you must remove all roaming or nonroaming stores at once; there is no way to remove individual stores. To remove all nonroaming stores, use the command storeadm /remove. To remove all roaming stores, use the command storeadm /roaming /remove.
|
| [ Team LiB ] |
|