| [ Team LiB ] |
|
14.1 Encryption RevisitedEncryption is the process of transforming a message so that it cannot be read if it is intercepted but can still be understood by the intended recipient. If Alice encrypts and sends a confidential message to Bob, Eve will not be able to make sense of what it says, and the contents of the message will remain confidential. Bob, as the intended recipient, is able to decrypt the message, which is the process of restoring the original message from the encrypted data. Like almost all types of cryptography, encryption relies on keeping a key secret from Eve. Figure 14-1 shows the basic model for modern data encryption. Alice uses an encryption algorithm to convert her message into encrypted data, which she sends to Bob. Bob uses a secret key to decrypt the data, transforming it back into the original message, which he then reads. Eve can intercept the encrypted data, but she is unable to read the original message unless she can acquire the secret key that Bob uses to decrypt the data or find a weakness in the encryption algorithm Alice used. Figure 14-1. Alice uses encryption to ensure message confidentiality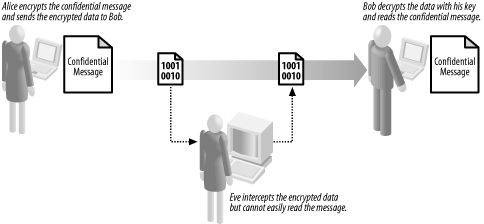 If Eve acquires the key, she will be able to decrypt the data in the same way that Bob does and read the message. She may be able to steal the key, or she may keep guessing until she finds the right key. If Eve is able to find a weakness in the algorithm Alice used, then she may be able to determine the contents of the confidential message without needing the secret key. In this chapter, we discuss the first of the two basic types of encryption, known as "symmetric" or "secret key" encryption. We cover the second type of encryption in Chapter 15. |
| [ Team LiB ] |
|