| [ Team LiB ] |
|
5.4 Introducing Isolated StorageMany applications need to store state or user preferences so that they are available the next time the application runs. Windows applications usually store this type of data in configuration files, the Windows registry, or external databases. For regularly used applications that are trusted, you will configure CAS security policy to give the application access to the required resource so that it can store this data successfully. However, because your hard disk, registry, and databases contain important information, it is unlikely that you will want to configure CAS to allow unknown and untrusted code to access them. Nor do you want to have to reconfigure security policy every time you install a new application or download mobile code from the Internet. Isolated storage provides a safe storage area on the hard disk where managed code can store noncritical data. The .NET runtime manages isolated storage to ensure that code cannot access other code's data and to limit the space used by each application. Most importantly, because the interfaces and CAS permissions that control access to isolated storage are different from those of normal file I/O, the risk of malicious code using isolated storage as a gateway through which to access other data on the hard drive is minimized. Figure 5-4 illustrates two managed applications that store data to the hard drive. Figure 5-4. Isolated storage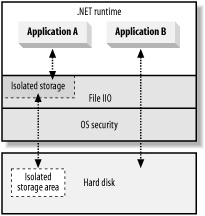
In Figure 5-4, Application A accesses its data through the .NET Framework's isolated storage mechanism, while Application B accesses the hard disk directly. We Provide a detailed discussion of isolated storage in Chapter 11. |
| [ Team LiB ] |
|