 |  |

Remote Logins
Windows from Other Computers
Lynx, a Text-based Web Browser
Transferring Files
Electronic Mail
Usenet News
Interactive Chat
A network lets computers communicate with each other, sharing files, email, and much more. Unix systems have been networked for more than 25 years.
This chapter introduces Unix networking: running programs on other computers, copying files between computers, browsing the World Wide Web, sending and receiving email messages, reading and posting messages to Usenet "Net news" discussions, and "chatting" interactively with other users on your local computer or worldwide.
The computer you log in to may not be the computer you need to use. For instance, you might have a workstation on your desk but need to do some work on the main computer in another building. Or you might be a professor doing research with a computer at another university. Your Unix system can connect to another computer to let you work as if you were sitting at that computer. This section describes how to connect to another computer from a local terminal. If you need to use a graphical (nonterminal) program, Section 6.2, next, explains.
To log into a remote computer using a terminal, first log in to your local computer (as explained in Section 1.1.2 in Chapter 1, or in Section 2.2.1 in Chapter 2). Then, in a terminal or terminal window on your local computer, start a program that connects to the remote computer. Some typical programs for connecting over a computer network are telnet, ssh ("secure shell"), rsh, ("remote shell") or rlogin ("remote login"). Programs such as cu and tip connect through telephone lines using a modem. In any case, when you log off the remote computer, the remote login program quits and you get another shell prompt from your local computer.
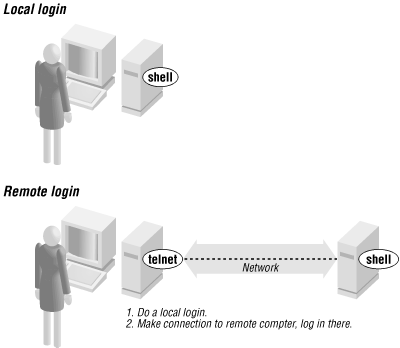
Figure 6-1 shows how remote login programs such as telnet work. In a local login, you interact directly with the shell program running on your local system. In a remote login, you run a remote-access program on your local system; that program lets you interact with a shell program on the remote system.
The syntax for most remote login programs is:
program-name remote-hostname
For example, when Dr. Nelson wants to connect to the remote computer named biolab.medu.edu, she'd first make a local login to her computer named fuzzy. Next, she'd use the telnet program to reach the remote computer. Her session would look something like this:
login: jennifer Password: NOTICE to all second-floor MDs: meeting in room 304 at 4 PM. fuzzy$ telnet biolab.medu.edu Medical University Biology Laboratory biolab.medu.edu login: jdnelson Password: biolab$ . . . biolab$ exit Connection closed by foreign host. fuzzy$
Her accounts have shell prompts that include the hostname. This reminds her when she's logged in remotely. If you use more than one system but don't have the hostname in your prompt, see Section 8.1 in Chapter 8 to find out how to add it.
NOTE: When you're logged on to a remote system, keep in mind that the commands you type will take effect on the remote system, not your local one! For instance, if you use lpr or lp to print a file, the printer it comes out of may be very far away.
The programs rsh (also called rlogin) and ssh generally don't give you a "login:" prompt. These programs assume that your remote username is the same as your local username. If they're different, give your remote username on the command line of the remote login program, as shown in the next example.
You may be able to log in without typing your remote password or passphrase.[16] Otherwise, you'll be prompted after entering the command line.
[16] In ssh, you can run an agent program, such as ssh-agent, that asks for your passphrase once, and then handles authentication every time you run ssh or scp afterward. For rsh and rcp, you can either store your remote password in a file named .rhosts in your local home directory, or the remote system can list your local computer in a file named hosts.equiv that's set up by the system administrator.
Following are four sample ssh and rsh command lines. (You may need to substitute rlogin for rsh.) The first pair show the way to log in to the remote system, biolab.medu.edu, when your username is the same on both the local and remote systems. The second pair show how to log in if your remote username is different (in this case, jdnelson); note that your version of ssh and rsh may support both syntaxes shown:
$ ssh biolab.medu.edu
$ rsh biolab.medu.edu
$ ssh [email protected]
$ rsh -l jdnelson biolab.medu.edu
Today's Internet, and other public networks, have users (called crackers; also erroneously called hackers) who try to break into computers and snoop on other network users. Most remote login programs (and file transfer programs, which we cover later in this chapter) were designed 20 years ago or more, when networks were friendly places with cooperative users. Those programs (many versions of telnet and rsh, for instance) make a cracker's job easy. They transmit your data across the network in a way that allows crackers to read it--and they either send your password along, visible to the crackers, or they expect computers to allow access without passwords.
SSH is different; it was designed with security in mind. If anything you do over a network (like the Internet) is at all confidential, you really should find SSH programs and learn how to use them. SSH isn't just for Unix systems! There are SSH programs that let you log in and transfer files between Microsoft Windows machines, between Windows and Unix, and more. A good place to get all the details and recommendations for programs is the book SSH: The Secure Shell, by Daniel J. Barrett and Richard Silverman (O'Reilly).

Copyright © 2003 O'Reilly & Associates. All rights reserved.